Security research Or Yair discovered a method to trick antivirus and endpoint security solutions into deleting legitimate files on Windows systems. Yair found out that he could manipulate endpoint detection and response and antivirus programs so that these programs would function as data wipers on Windows devices.
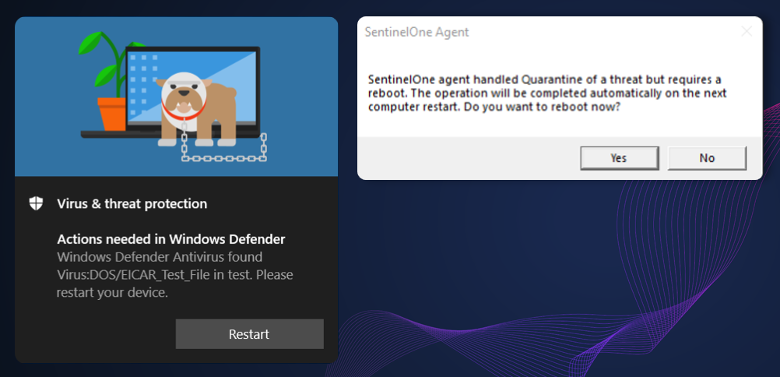
The discovered security issue can be exploited from unprivileged user accounts to delete system files and other files the user has no delete permissions for. The exploit could be used to remove important files from a system and this could result in an unbootable system or a system that lacks certain functionality.
Classified as a data wiper, a class of malware designed to erase data on computer systems, its main purpose is destruction. Wipers are commonly used in cyber warfare, often to support physical aggression or to target the enemy's infrastructure.
Wipers need to bypass certain protections, including those provided by a user permission system but also defenses that are in place to protect against unauthorized deletions of files. Additionally, to make sure that files can't be recovered, wipers need to overwrite file contents.
Endpoint security and antivirus solutions would make excellent file wipers, if security issues could be exploited to use their privileges and capabilities. Yair had several ideas in this regard, but most were not practicable. Some required elevated privileges, others write access to the files in question.
The main idea that he came up with was to create a malicious file in a temporary directory, and to redirect it to an important file on the system between the time the security solution detected the threat and deleted it. This method did not work out as planned initially, as some security solutions prevented access to detected files while others detected the deletion of the file and dismissed the pending action.
Yair's solution was to keep the file open, so that it could not be deleted by the security solutions right away. The security programs would prompt for a reboot in that case so that the malicious file could be accessed and deleted. Files are added to a specific key in the Registry, so that Windows knows what to delete during the boot phase. Yair discovered that the deletion process would follow junctions, created to point the delete operation to a legitimate file.
In other words, all it took to delete legitimate files on Windows was the following:
- Create a malicious file on the system using a special path.
- Hold it open so that security solutions can't delete it.
- Delete the directory.
- Create a junction that points from the deleted directory to another.
- Reboot.
Yair tested 11 different security and endpoint solutions. Six of these were vulnerable to the file wiping exploit, including Microsoft Defender, Microsoft Defender for Endpoint, Avast Antivirus, SentinelOne EDR and TrendMicro Apex One. Microsoft, TrendMicro and Avast/AVG released updates already to address the issue.
Now You: which security solution(s) do you use? (via Bleeping Computer)
Thank you for being a Ghacks reader. The post Tricking antivirus solutions into deleting the wrong files on Windows appeared first on gHacks Technology News.

0 Commentaires