Microsoft plans to roll out new default settings in the next major Windows 11 release that delay brute force attacks against accounts on the system.
Brute-force attacks are commonly used by threat actors to gain access to systems. Especially Remote Desktop Protocol attacks are frequently used to gain remote access to Windows machines. Microsoft notes that human-operated ransomware attacks use Remote Desktop Protocol brute force attacks frequently to break into accounts.
One of the main shortcomings of Windows is that there is no default limitation that delays brute force attacks. While organizations may implement additional protections, e.g., by going passwordless or enabling two-factor authentication, most Windows systems are not protected against attacks.
Launched in the latest Windows 11 Insider builds and coming soon to all Windows 11 devices is a set of new account lockout policies that improve brute forcing protection on the operating system.
The protections delay brute force attacks by locking accounts after a number of failed login attempts. The default configuration locks accounts after 10 invalid login attempts for 10 minutes. The protection is available for all account types, including administrator accounts, by default.
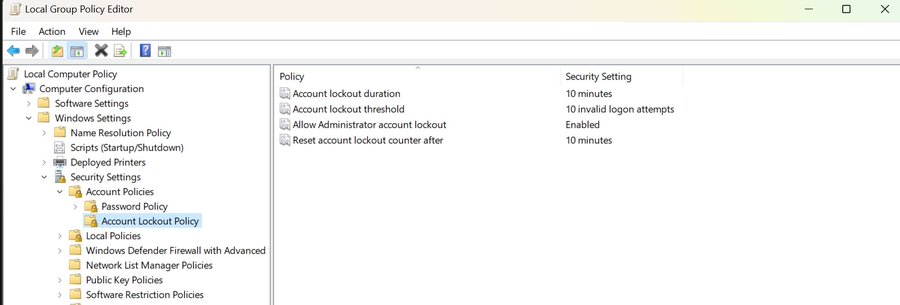
Windows 11 administrators may change the default configuration using the Group Policy Editor:
- Use Windows-R to open the run box.
- Type gpedit.msc and hit the Enter-key to load the Group Policy Editor.
- Navigate to Local Computer Policy > Computer Configuration > Windows Settings > Security Settings > Account Lockout Policy.
- A double-click on any of the four listed policies displays options to change the default values.
The four policies in question are:
- Account lockout duration -- defines the time that the account will be locked if too many invalid login attempts are logged by the Windows 11 system.
- Account lockout threshold -- defines the number of failed login attempts that Windows uses to determine whether the account should be locked.
- Allow Administrator account lockout -- whether admin accounts should be locked as well.
- Reset account lockout counter after -- when the lockout counter is reset.
Closing Words
Microsoft plans to launch the new brute force protections in the next feature update, which is scheduled for a release in the coming months. The new defaults should limit human-operated ransomware attacks that try to brute force their way into Windows PCs significantly.
Now You: what is your take on this new protection?
Thank you for being a Ghacks reader. The post Next Windows 11 delays brute force attacks by default appeared first on gHacks Technology News.
0 Commentaires